[ad_1]
Governance and Risk Management, Operational Technology (OT)
Microsoft confirmed the 2021 report, saying 1 million Boa servers are still online worldwide
Mihir Bagwe (MihirBagwe) •
November 23, 2022

A nearly 20-year-old, outdated web server is likely responsible for last month’s hack on India’s largest integrated power company, Tata Power, Microsoft said.
See more: Live Webinar | How to Achieve Your Zero Trust Goals Through Advanced Endpoint Strategies
Stopped in 2005, the Boa server was used to target and compromise several other critical infrastructure organizations around the world, Microsoft said in its security blog.
Online digital threat analysis firm Recorded Future first reported in 2021 that a state-sponsored Chinese group was responsible for infecting India’s power supply company with malware (see: India Fights Against Malware Targeting Power Supply).
The Microsoft Threat Intelligence Center warned that Boa servers run on IP addresses found in a list of IOCs published last year by Recorded Future and grid attacks targeting exposed IoT devices running on Boa servers.
On October 14, Tata Power revealed that a cyber attack had hit its IT infrastructure affecting some of its IT systems. The attack did not affect its operations, but as a preventive measure, the utility limited access and implemented security checks for employees and doors and touch points, a company spokesperson told the Information Security Media Group at the time.
Later that month, the Hive ransomware gang posted the data on the leaked dark web and claimed that the data had been stolen from Tata Power’s network.
The stolen information includes employee information such as email, address, passport, phone number, payment, working hours, taxpayer information, signed confidentiality agreements, non-disclosure agreements and other sensitive documents, the Hive ransomware gang claimed on its leaked website.
The Hive ransomware gang uses a Ransomware-as-a-Service model where its affiliates are known to target critical infrastructure. Hive operators have hit more than 1,300 companies around the world, collecting about $100 million in ransom payments, a recent joint alert from the Cybersecurity and Infrastructure Agency, the FBI and the Department of Health and Human Services said (see: Feds Alert Healthcare, Others. Sectors Growing Threats Hive).
A Tata Power spokesperson declined to comment on the group’s claims and Microsoft’s latest findings.
However, in a November 24 update, a Microsoft spokesperson told ISMG that it “did not specifically identify” the Tata Power attack with the Boa exploit, despite linking to a news story about the October cyber attack in its blog post. “The recent attack on Tata Power is evidence of a trend to target the assets and operations of India’s electricity grid. Microsoft’s blog post uses data from Recorded Future’s April 2022 report on hacking activity in India’s critical infrastructure, and presents Microsoft’s findings,” the spokesperson explained.
Boa Server Vulnerability
Although it was officially discontinued in 2005, the Boa web server is still widely implemented across many IoT devices including routers to cameras, Microsoft said. These findings confirm the report of Recorded Future, which said that the threat group may have compromised an undisclosed Indian energy company and exploited and cooperated with Internet-facing DVR/IP camera equipment for command and control to spread the ShadowPad malware infection.
Microsoft Defender Threat Intelligence identified more than 1 million Boa server components exposed to the global Internet over the course of a week.
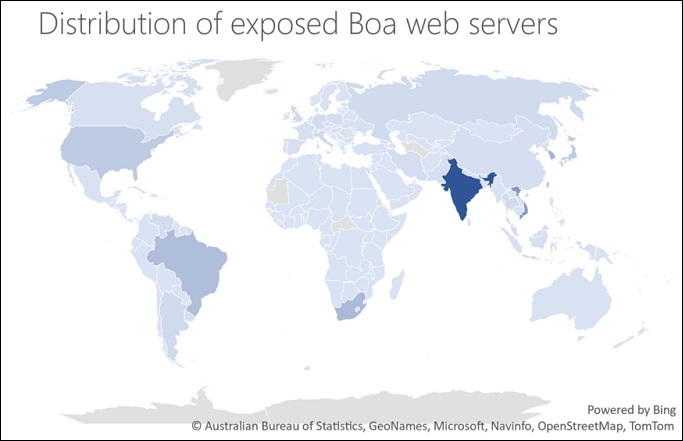
Exploiting these vulnerabilities is particularly relevant because attackers do not require authentication to exploit them, making them an attractive target. The vulnerability also allows an attacker to execute remote code after gaining read access to the device passwd files from the device and help exfiltrate important server and user data.
Boa servers are often used to access the configuration and management consoles as well as the login screens of these devices.
“Boa servers are affected by several known vulnerabilities, including arbitrary file access (CVE-2017-9833) and data disclosure (CVE-2021-33558),” Microsoft said.
[ad_2]
Source link











